
Businesses and enterprises often fall into the bad habit of turning compliance into an annual task of checking boxes. Going through audits or filling out self-assessments is necessary to avoid paying fines and, in some cases, to continue to operate. However, a check-box view of compliance does nothing to strengthen your security framework.
The Purpose of Compliance
Standards and regulations, such as the Health Insurance Portability and Accountability Act (HIPAA), Payment Card Industry (PCI), Service Organization Control (SOC) 2 Type II, or Federal Financial Institutions Examinations Council (FFIEC), are based on security best practices for businesses or organizations like yours. Each compliance requirement is meant to make your IT environment more secure – and in a world where cyberattacks are becoming more frequent, more expansive, and more complex (e.g., the SolarWinds hack), stronger security should be a priority for everyone.Compliance’s Link to a Security Framework
When you dig deeper into compliance requirements, you can see the correlation between compliance and security. For example, the FFIEC Cybersecurity Assessment Tool breaks down security into five domains: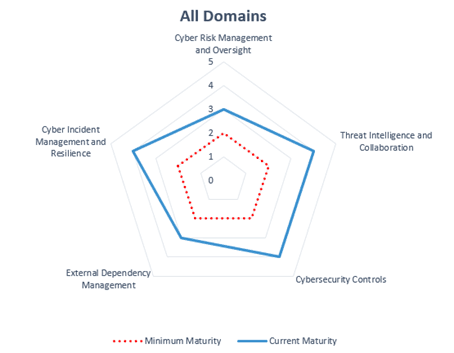
- Cyber Risk Management and Oversight
- Threat Intelligence and Collaboration
- Cybersecurity Controls
- External Dependency Management
- Cyber Incident Management and Resilience
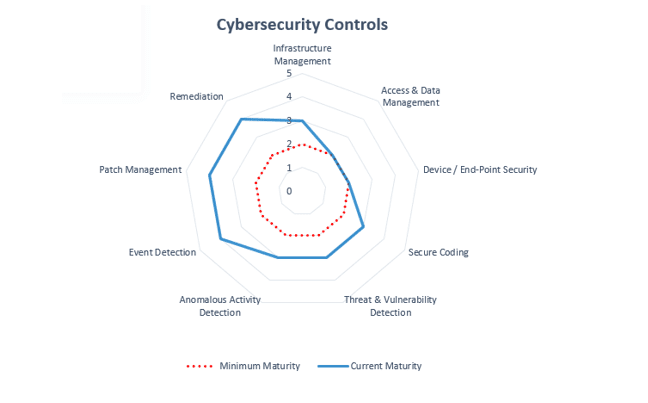
- Infrastructure Management
- Access & Data Management
- Device/End-Point Security
- Secure Coding
- Threat & Vulnerability Detection
- Anomalous Activity Detection
- Event Detection
- Patch Management
- Remediation
- “Baseline”
- “Evolving”
- “Intermediate”
- “Advanced”
- “Innovative”
- Have a firewall and other perimeter controls
- Systems that are connected to the internet are protected
- Ports are monitored
- Antivirus and antimalware are up to date
- You follow industry standards to configure systems
- Ports that aren’t used are disabled
- Access to make changes to configurations are monitored
- Programs that can override security systems are restricted
- Sessions are locked or terminated after a predefined timeframe
- Wireless networking has security settings and encryption
Visualizing Security Framework Maturity
FFIEC also recognizes that building a strong security framework is a continuing process. Visualizations can help you and your team see your business or organization’s current maturity, how it compares to minimum maturity – and how much progress you need to make.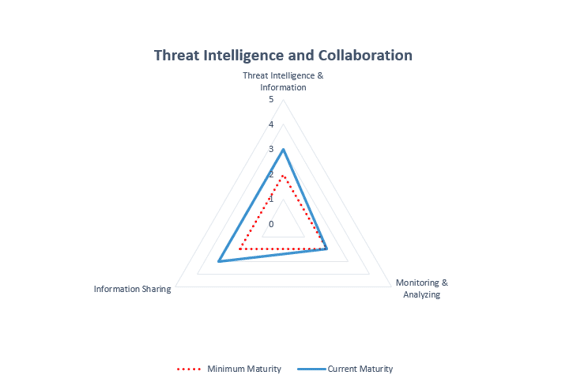 In this framework, many businesses and organizations find themselves in the 1-2 range but all will find areas where they can improve and make changes that will make their organizations more secure.
In this framework, many businesses and organizations find themselves in the 1-2 range but all will find areas where they can improve and make changes that will make their organizations more secure.
Break the Cycle of Compliance for Compliance’s Sake
When you first look at a compliance assessment tool or an audit report, it’s easy to be overwhelmed, but just quickly running through the list of requirements and checking boxes isn’t providing your business or organization with the greatest degree of security. Compliance is meant to provide your business with a security framework that will protect your data, customers, systems, and, ultimately, your business from the devastating impacts of a data breach. Many business leaders know their organizations are vulnerable to cyberattacks but don’t know how to address the problem. Compliance audits and assessment tools are an excellent place to start.Share
Resources + Updates